
Google’s Risk Analysis Group (TAG) has actually been keeping track of and interrupting Russian state-backed cyberattacks targeting Ukraine’s important facilities in 2023.
Google reports that from January to March 2023, Ukraine got approximately 60% of the phishing attacks stemming from Russia, making it the most popular target.
Most of the times, the project objectives consist of intelligence collection, functional interruptions, and dripping delicate information through Telegram channels devoted to triggering details damage to Ukraine.
Risk groups active in Ukraine
Google’s TAG lists 3 Russian and Belarusian hazard stars who had significant activity in the very first quarter of the year versus Ukrainian targets.
The very first is Sandworm, tracked by Google as “FrozenBarents,” which has actually focused its attacks on the energy sector throughout Europe considering that November 2022, with a highlighted case including the Caspian Pipeline Consortium (CPC).
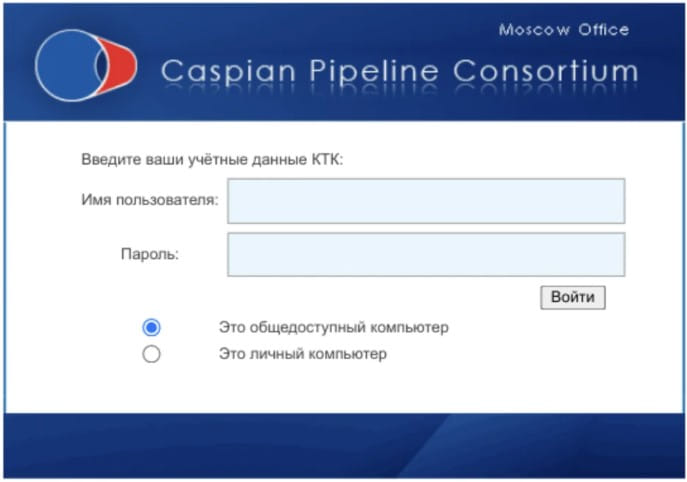
Sandworm has actually recently released several phishing projects utilizing spoofed “Ukroboronprom” sites versus employees in the Ukrainian defense market, users of the Ukr.net platform, and even Ukrainian Telegram channels.

The hazard group likewise develops several online personalities to share incorrect details on YouTube and Telegram, frequently dripping parts of the information they take through phishing or network invasions.
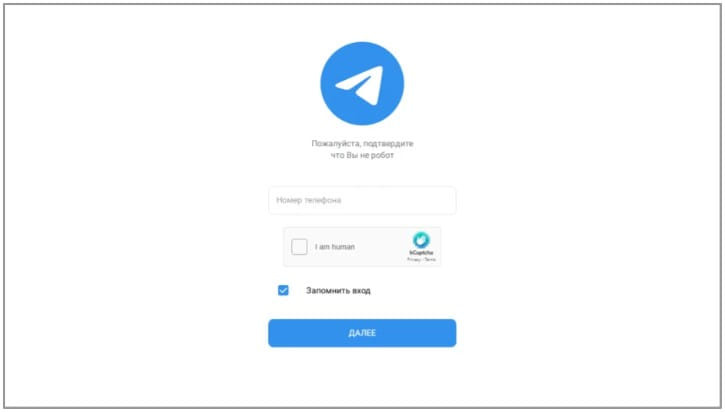
Another highly-active Russian hazard star is APT28, tracked by Google as “FrozenLake.”
In Between February and March 2023, APT28 sent several big waves of phishing e-mails targeting Ukrainians. The hackers likewise utilized shown cross-site scripting (XSS) on Ukrainian federal government sites to reroute visitors to phishing pages.

Today, a joint statement by the UK NCSC, FBI, NSA, and CISA alerted that APT28 is hacking Cisco Routers to set up customized malware
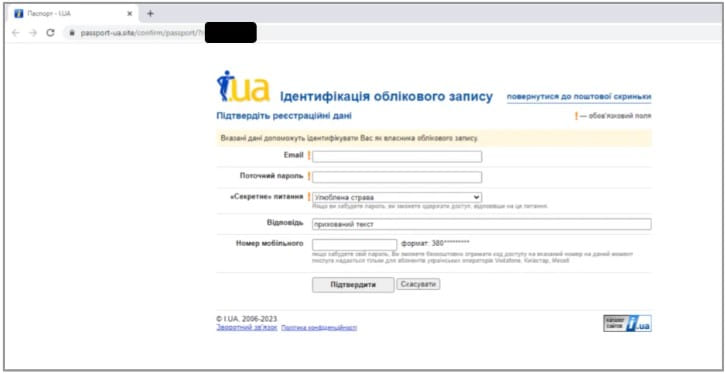
The 3rd hazard star highlighted in Google’s report is “Pushcha,” which is thought to be based in Belarus, a nation that is politically lined up with the Kremlin.
Pushcha has actually just recently released projects that target Ukrainian webmail companies like “i.ua” and “meta.ua,” trying to take the users’ qualifications by establishing fake websites.
State-funded false information
Google’s report likewise highlights cases of false information on its platforms, like YouTube and Blog writer.
” In the very first quarter of 2023, TAG observed a collaborated IO project from stars connected with the Web Research Study Company (INDIVIDUAL RETIREMENT ACCOUNT) developing material on Google items such as YouTube, consisting of commenting and upvoting each other’s videos,” checks out the Google TAG report
The Individual Retirement Account (Glavset) is a Russian business connected to Wagner Group’s owner, Y. Prigozhin, taking part in online propaganda and affect operations on behalf of Russian political interests.
Google reports that it has actually been observing and obstructing IRA-linked accounts developing material on YouTube Shorts to promote particular “news-like” stories about the war in Ukraine to Russian domestic audiences.
All sites connected to the discussed projects have actually been contributed to Google’s “Safe Surfing” blocklist, while targeted Gmail and Work space users got notifies informing them about destructive interactions.