
New IcedID variants were discovered with out the standard on-line banking fraud capability and as an alternative center of attention on putting in additional malware on compromised programs.
In step with Proofpoint, those new variants were observed utilized by 3 distinct danger actors in seven campaigns since past due ultimate yr, specializing in additional payload supply, maximum significantly ransomware.
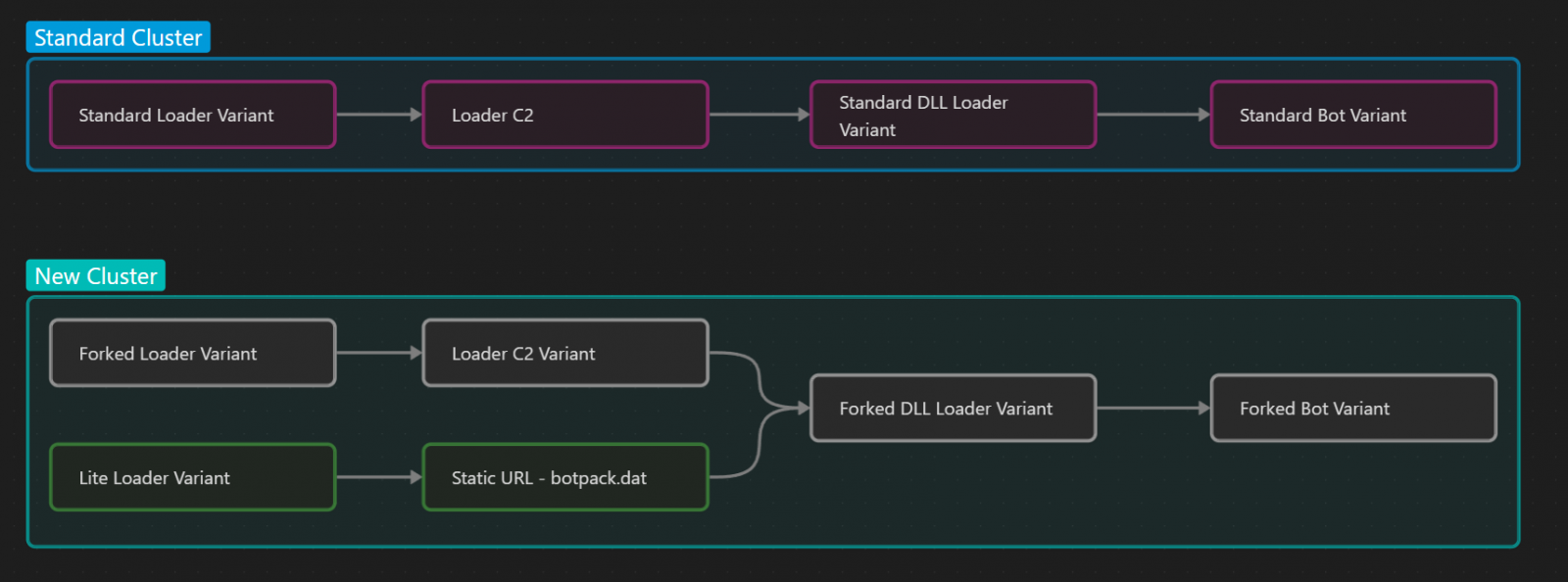
Proofpoint has known two new variants of the IcedID loader, specifically âLiteâ (first observed in November 2022) and âForkedâ (first seen in February 2023), each handing over the similar IcedID bot with a extra narrow-focused characteristic set.
Putting off unneeded purposes on IcedID, which has been deployed in a large number of malicious campaigns with out many code adjustments since 2017, makes it stealthier and leaner, which is able to lend a hand the danger actors evade detection.
New IcedID campaigns
Beginning in November 2022, the âLiteâ variant of the IcedID loader used to be delivered as a second-stage payload on programs inflamed via the newly-returned Emotet malware.
The âForkedâ model of the malware loader first seemed in February 2023, allotted without delay via 1000’s of customized invoice-themed phishing emails.
Those messages used Microsoft OneNote attachments (.one) to execute a malicious HTA document that, in flip, runs a PowerShell command which fetches IcedID from a faraway useful resource. On the identical time, the sufferer is served a decoy PDF.

On the finish of February, Proofpointâs researchers seen a low-volume marketing campaign distributing IcedID âForkedâ by way of pretend notices from the Nationwide Visitors and Motor Car Protection Act and the U.S. Meals and Drug Management (FDA).
You will need to notice that whilst some danger actors use new variants of the IcedID malware, others nonetheless make a selection to deploy the âUsualâ variant, with one of the crucial contemporary campaigns courting March 10, 2023.
The brand new variants
The âForkedâ IcedID loader is reasonably very similar to the âUsualâ model on the subject of its position, sending fundamental host information to the C2 after which fetching the IcedID bot.Â
On the other hand, âForkedâ makes use of a special document sort (COM Server) and contours further area and string-decryption code, making the payload 12KB higher than the âUsualâ model.
Then again, the âLiteâ loader variant is lighter, at 20KB, and does now not exfiltrate host information to the C2. This modification is smart because it used to be deployed along Emotet, which had already profiled the breached device.
The âForkedâ model of the IcedID bot is 64KB smaller than the âUsualâ bot, and is mainly the similar malware minus the internet injects device, the AiTM (adversary within the heart) purposes, and the backconnect features that give danger actors faraway get entry to to inflamed gadgets.
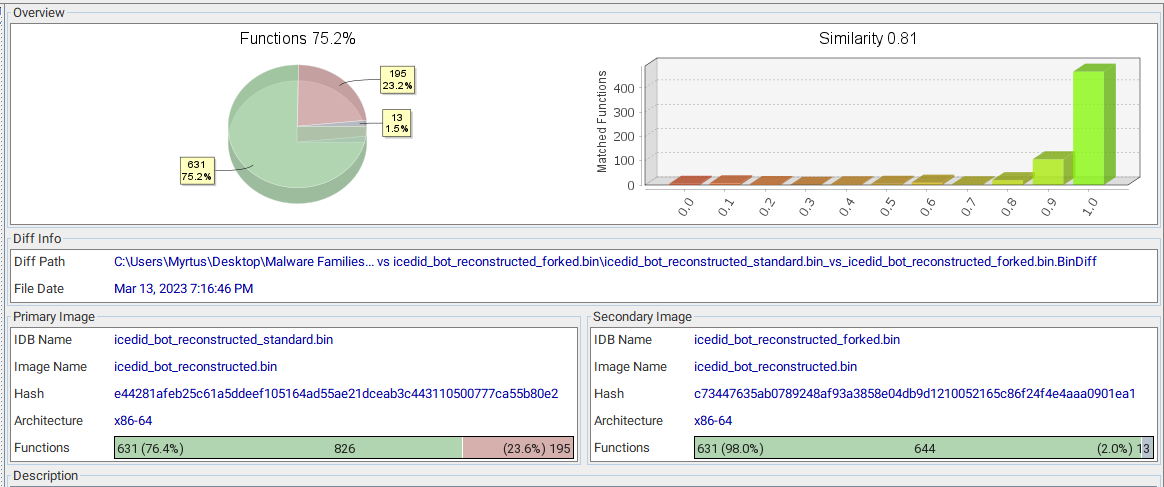
IcedID is typically used for preliminary get entry to via danger actors, so creating new variants is a being worried signal, signifying a shift against specializing the bot to payload supply.
Proofpoint predicts that almost all danger actors will proceed to make use of the âUsualâ variant, however the deployment of latest IcedID variations will most probably develop, and extra variants would possibly pop up later in 2023.