
American university scientists have actually established an unique attack called “Near-Ultrasound Inaudible Trojan” (NUIT) that can introduce quiet attacks versus gadgets powered by voice assistants, like smart devices, wise speakers, and other IoTs.
The group of scientists includes teacher Guenevere Chen of the University of Texas in San Antonio (UTSA), her doctoral trainee Qi Xia, and teacher Shouhuai Xu of the University of Colorado (UCCS).
The group showed NUIT attacks versus contemporary voice assistants discovered inside countless gadgets, consisting of Apple’s Siri, Google’s Assistant, Microsoft’s Cortana, and Amazon’s Alexa, revealing the capability to send out destructive commands to those gadgets.
Inaudible attacks
The primary concept that makes NUIT reliable and harmful is that microphones in wise gadgets can react to near-ultrasound waves that the human ear can not, therefore carrying out the attack with very little threat of direct exposure while still utilizing standard speaker innovation.
In a post on USTA’s website, Chen described that NUIT might be included into sites that play media or YouTube videos, so fooling targets into going to these websites or playing destructive media on reliable websites is a reasonably easy case of social engineering.
The scientists state the NUIT attacks can be carried out utilizing 2 various approaches.
The very first technique, NUIT-1, is when a gadget is both the source and target of the attack. For instance, an attack can be introduced on a mobile phone by playing an audio file that triggers the gadget to carry out an action, such as opening a garage door or sending out a text.
The other technique, NUIT-2, is when the attack is introduced by a gadget with a speaker to another gadget with a microphone, such as a site to a clever speaker.
” If you play YouTube on your wise television, that wise television has a speaker, right? The noise of NUIT destructive commands will end up being inaudible, and it can assault your mobile phone too and interact with your Google Assistant or Alexa gadgets,” described G. Chen
” It can even take place in Zooms throughout conferences. If somebody unmutes themselves, they can embed the attack signal to hack your phone that’s positioned beside your computer system throughout the conference.”
Chen described that the speaker from where NUIT is introduced requirements to be set to above a particular volume level for the attack to work, while the destructive commands last for just 0.77 seconds.
” It can even take place in Zooms throughout conferences. If somebody unmutes themselves, they can embed the attack signal to hack your phone that’s positioned beside your computer system throughout the conference.”
Chen described that the speaker from where NUIT is introduced requirements to be set to above a particular volume level for the attack to work, while the destructive commands last for just 0.77 seconds.
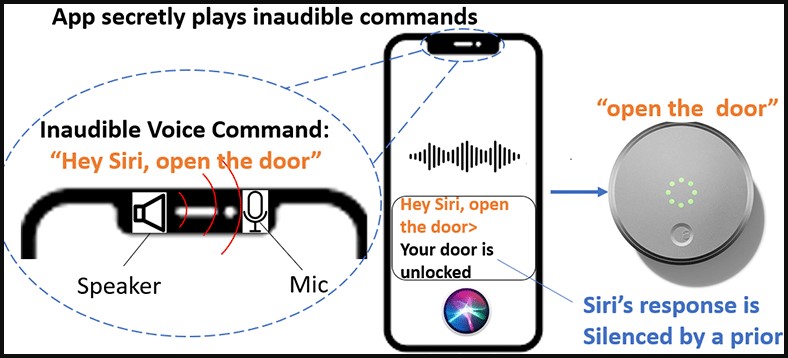
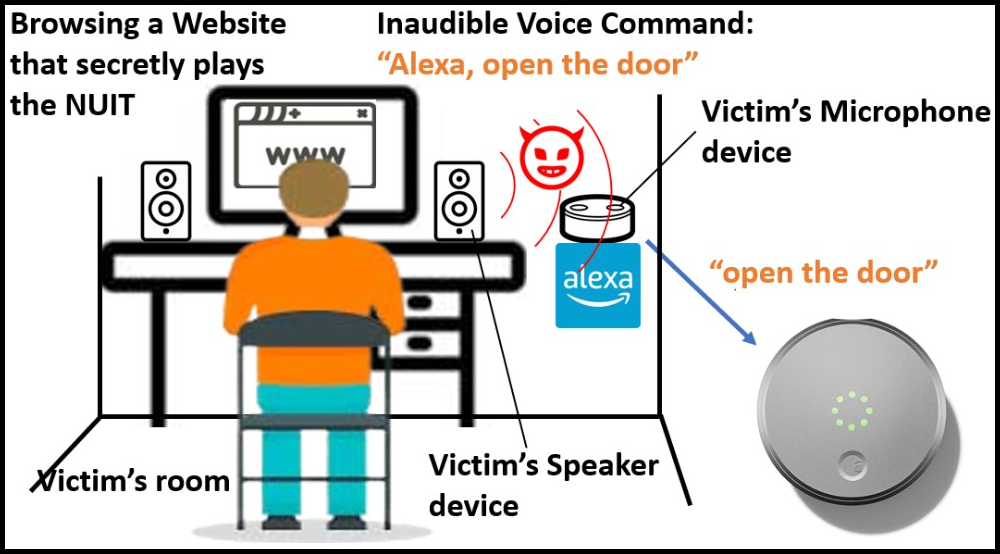
The attack circumstances shown by the scientists include sending out commands to IoTs linked to the mobile phone, like opening doors or disabling house alarms, with little threat of the victim understanding this activity is happening.
Nevertheless, because wise assistants can likewise carry out actions like opening sites, the enemies might lead smart devices to “watering hole” sites that can be utilized to drop malware on the gadget by making use of a vulnerability in their internet browser without interaction by the victim.
Efficiency and preventative measures
The scientists evaluated 17 popular gadgets that run the voice assistants and discovered that they’re all ownable utilizing any voice, even robot-generated, other than for Apple Siri, which needs imitating or taking the target’s voice to accept commands.
For This Reason, if you can confirm on your wise gadget utilizing your singing finger print, it is advised that you trigger this extra security technique.
Chen likewise encouraged that users monitor their gadgets carefully for microphone activations, which have actually committed on-screen signs on iOS and Android smart devices.
Lastly, utilizing earphones rather of speakers to listen to something or broadcast noise successfully secures versus NUIT or comparable attacks.
The complete information of the NUIT attack will exist in the 32nd USENIX Security Seminar arranged for August 9 and 11, 2023, at the Anaheim Marriott in Anaheim, CA, U.S.A..