Summary:
- Over-privileged accounts create security vulnerabilities by expanding an organization’s attack surface
- Rockset has released new security features that allow admins to limit access to certain users to a specific subset of data without exposing the complete data set
- RBAC with Custom Roles enables admins to create scoped down user roles with limited privileges. Roles can now be assigned to API Keys so privileges through the API Key are defined by the role
- View is a virtual collection defined by a SQL query that enables admins to expose limited data set to customers
- Rockset enhances real-time analytics with enterprise-grade security and compliance
“The last thing you want is to be on the front page of the WSJ because of a breach.”
This quote has stayed with me ever since I started working in enterprise security. Enterprises today are very conscious and deliberate about security requirements with every third-party vendor they choose to work with. Because customer trust is always a core value and top priority, successful enterprises are establishing trust by ensuring that their customers’ data is always kept private and secure.
At Rockset, we serve enterprise customers from a wide range of industries, and all of them inquire about our security capabilities and how we handle their data. Security is top of mind for us just like it is for our customers. This manifests itself in our strong security features and focus on the various security measures we take including SOC 2 Type II compliance, data masking, advanced encryption for data in flight and at rest, and advanced access controls such as native multi-factor authentication and integrations with SSO providers like Okta. For complete info on how Rockset keeps itself and its customers safe, visit the Rockset Security Whitepaper.
A joint study from Stanford University and security firm Tessian revealed that nine out of 10 data breaches are caused by employees’ mistakes. For that reason, providing employees with only the bare minimum access they need to perform their jobs is fundamental to protecting both company data and customer data. Role-Based Access Control (RBAC) is commonly how companies achieve the principle of ‘least privilege’ — providing access to the right people (or services) at the right time, for the right resources.
Fine-Tuned Control with RBAC Custom Roles
Until now, our RBAC feature was limited to a handful of built-in roles for both users and API keys they created (which inherited their role). Those built-in roles were unable to satisfy the various needs of our customers for full access controls, especially when customers used Rockset in their customer-facing applications.
A common use-case we hear customers ask is to limit data access via a Query Lambda with an API key. In the past, a developer using Rockset wasn’t able to create an API key that only allowed read access to a subset of data. Developers would have to use custom code within their application to restrict access. This was not scalable and customers told us they wanted a more robust way to limit access, both to the Rockset console and it’s API keys.
After listening to what our developers needed, we went back to the drawing board and identified access privileges for every single action on every single resource within Rockset. This would enable us to ultimately build Role-Based Access Control with Custom Roles, the feature we have today that allows our customers to create and control granular and intuitive access controls across Rockset.
Here is a sample custom role within the Rockset admin console:
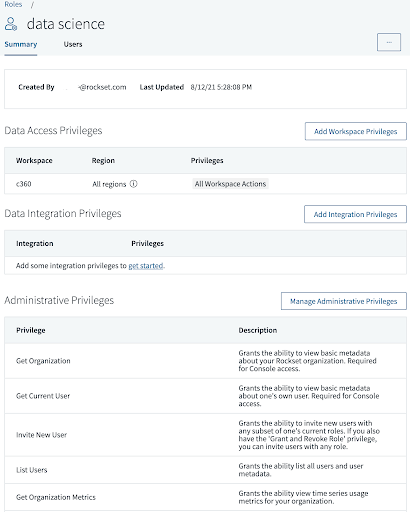
As you can see, there are three different sections: Data Access, Data Integration, and Administrative Privileges. Each section has a different list of privileges that you can assign a user. You can further segment data access by letting users read or write data to only certain Workspaces. These Workspaces are like folders, and can contain Collections, Aliases, Query Lambdas, and Views.
Here is a demo of Role-Based Access Control with Custom Roles:
Embedded content: https://youtu.be/NJxshf2YQy4
Share Only a Subset of Data with Views
Did you notice that a custom role can now manage Views? If you’re surprised to see Views on the above list of resources included in a Workspace, it’s because View is another new feature we’re launching! Views are stored, pre-defined SQL queries that can be queried like all other persistent data in Rockset. It’s a virtual, controllable look at data that protects the underlying dataset. Views further enhances how data is accessed within Rockset or by applications that use Rockset as the data serving layer.
Before Views, a common security challenge for our customers was that after a Collection was ingested into Rockset, it still might contain sensitive data that some employees or customers shouldn’t be able to query. Yet, there was no way to expose only a subset of data to those employees or customers. Now, with Views, you can allow those users access to that scoped down data set without the need to reingest the entire data set to another Collection.
Furthermore, if you want to apply SQL logic before the data is served to the app, you can now do this with Views, allowing your users to immediately get the answers they are looking for.
Here’s what a View looks like in our console:
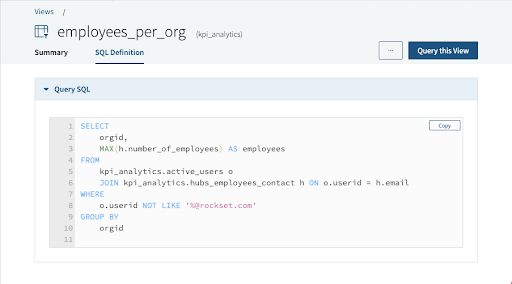
In the examples above, the employees_per_org View can be further queried just like any other collection in Rockset, including using JOINs. It can also be used in the definition of a Query Lambda the same way that Collections are. Views are not only great for restricting data access, but they are also great for modularizing your queries. If you have a CTE (Common Table Expression) you often use in various queries, you can now replace it with a View, and not worry about updating that CTE multiple times across all those queries.
Here is a demo of Views:
Embedded content: https://youtu.be/CgoUJs20Vzk
Start Using Role-Based Custom Roles and Views Today
Managing Role-Based Custom Roles and Views is very intuitive. If you want to apply access controls to an application accessing Rockset through Query Lambdas or REST APIs, you simply assign the corresponding role to a given API key. Every user in our system can create an API key and apply the right level of access privileges for that key. Users can’t create an API key with privileges they don’t have themselves.
In addition to improving security, RBAC Custom Roles and Views also improve application speeds by removing the need for an intermediate service layer to manage API permissions.
In summary, RBAC Custom Roles and Views are new security features that provide powerful access controls for our customers. The granularity can be to any action performed on any resource on any subset of the data hosted in Rockset. With these two features combined, our customers can apply the concept of ‘least privilege’ on Rockset and rest assured that their customers’ data is only accessed when, where, and by only the necessary people and services. Both are available today so give them a try! For more details on the features, please view our product documents for RBAC and product documents for Views.