
Hackers are actively making use of an unpatched 2018 authentication bypass vulnerability in exposed TBK DVR (digital video recording) gadgets.
DVRs are an essential part of security monitoring systems as they tape-record and save video tape-recorded by video cameras. TBK Vision’s site declares its items are released in banks, federal government companies, the retail market, and more.
As these DVR servers are utilized to save delicate security video footage, they are typically found on internal networks to avoid unapproved access to the tape-recorded video. Regrettably, this makes them appealing to hazard stars who can exploit them for preliminary access to business networks and to take information.
Fortinet’s FortiGard Labs reports seeing an uptick in hacking efforts on TBK DVR gadgets just recently, with the hazard stars utilizing a openly readily available evidence of principle (PoC) make use of to target a vulnerability in the servers.
The vulnerability is a crucial (CVSS v3: 9.8) defect, tracked as CVE-2018-9995, which allows assailants to bypass authentication on the gadget and gain access to the affected network.
The make use of utilizes a maliciously crafted HTTP cookie, to which susceptible TBK DVR gadgets react with admin qualifications in the type of JSON information.
” A remote assailant might have the ability to exploit this defect to bypass authentication and get administrative benefits, ultimately leading access to video camera video feeds,” checks out an break out alert by Fortinet.
The vulnerability affects the TBK DVR4104 and TBK DVR4216 and rebrands of these designs offered under the Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night OWL, DVR Login, HVR Login, and MDVR brand names.
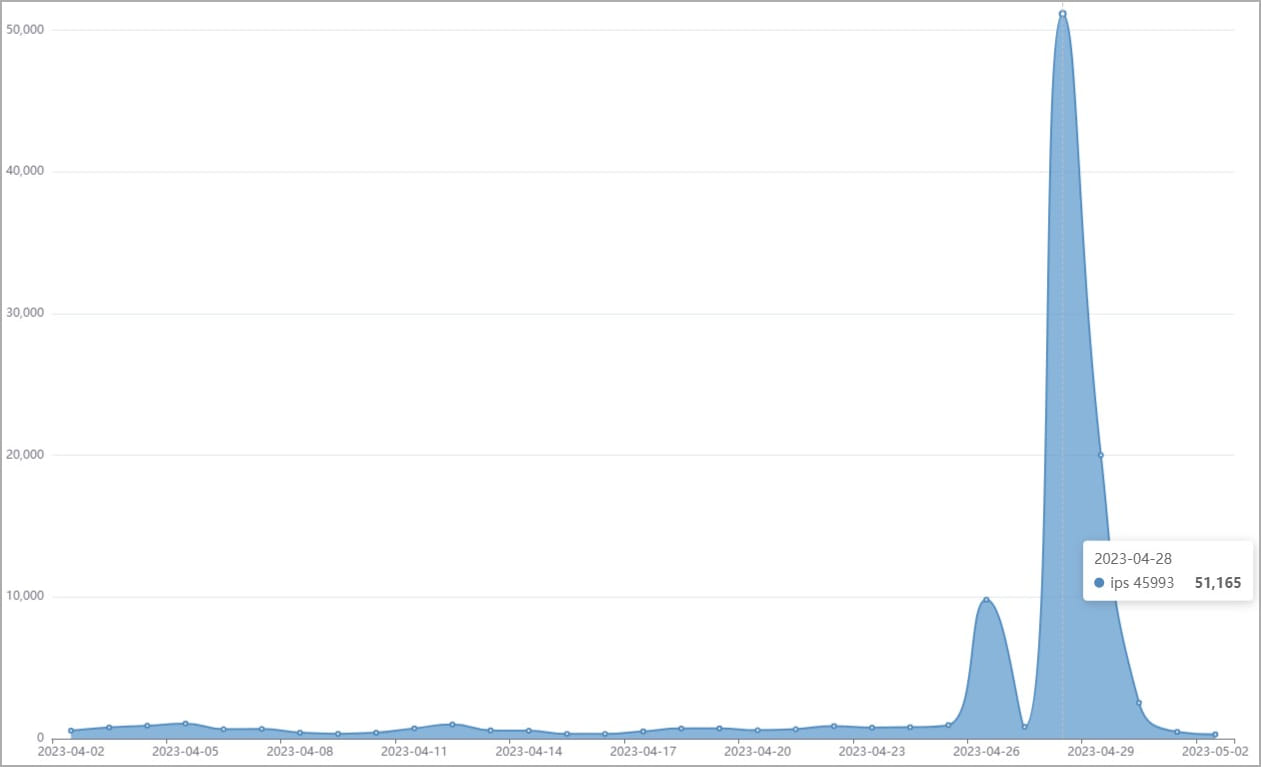
According to Fortinet, since April 2023, there were over 50,000 efforts to make use of TBK DVR gadgets utilizing this defect.
” With 10s of countless TBK DVRs readily available under various brand names, publicly-available PoC code, and an easy-to-exploit makes this vulnerability a simple target for assailants,” describes Fortinet.
” The current spike in IPS detections reveals that network video camera gadgets stay a popular target for assailants.”
Regrettably, Fortinet is uninformed of a security upgrade to attend to CVE-2018-9995. For that reason, it is recommended to change the susceptible security systems with brand-new and actively supported designs or separate them from the web to avoid unapproved gain access to.
Another old defect going through an exploitation “break out” is CVE-2016-20016 ( CVSS v3: 9.8, “important”), a remote code execution vulnerability affecting MVPower TV-7104HE and TV-7108HE DVRs, enabling assailants to carry out unauthenticated command execution utilizing destructive HTTP demands.
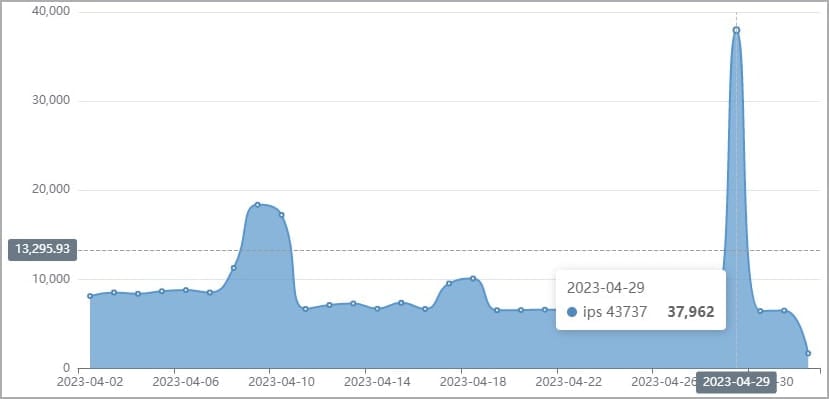
This defect has actually been under active exploitation in the wild considering that 2017, however Fortinet has actually just recently seen indications of increasing destructive activity leveraging it. In this case, too, the supplier has actually not provided a spot to repair the vulnerability.